Summary
On the 15th of May, 2024, Sonne Finance was attacked resulting in a loss of more than $20 million.
About Project
Sonne Finance is a decentralized lending protocol for individuals, institutions and protocols to access financial services. It is a permissionless, open source and Optimistic protocol serving users on Optimism. Users can deposit their assets, use them as collateral and borrow against them.
To learn more about Sonne Finance, head over to https://docs.sonne.finance/
Vulnerability Analysis & Impact
On-Chain Details
Attacker Address: 0xae4a7cde7c99fb98b0d5fa414aa40f0300531f43
Attacker Contract: 0x02fa2625825917e9b1f8346a465de1bbc150c5b9
Victim Contract: 0xe3b81318b1b6776f0877c3770afddff97b9f5fe5
Attack Transactions - https://optimistic.etherscan.io/tx/0x9312ae377d7ebdf3c7c3a86f80514878deb5df51aad38b6191d55db53e42b7f0
The Root Cause
Sonne Finance recently passed a proposal to add VELO markets to the protocol.
They scheduled the transactions on multisig wallet, and because there is a 2 day timelock, we also scheduled c-factors to be executed in 2 days. https://optimistic.etherscan.io/tx/0x18ebeb958b50579ce76528ed812025949dfcff8c2673eb0c8bc78b12ba6377b7
Their multisig execution is not permissionless on Base, but permissionless on Optimism.
The exploiter executed 4 of the transactions when the 2-day timelock ended for the creation of markets, and after that, executed the transaction for adding c-factor to the markets :
After the execution of the markets without the Sonne team noticing, the attacker was able to exploit the protocol for ~$20M with the known donation attack.
Attack Process
The attack process was as follows:
- The attacker obtained a flash loan of 35,569,150 VELO and moved these VELO Tokens to the soVELO contract. Since it was a direct transfer (donation), no soVELO Tokens were minted. As a result, the totalCash in the soVELO contract increased by 35,569,150 VELO, while the totalSupply of soVELO stayed the same.
The attacker created a new contract 0xa16388a6210545b27f669d5189648c1722300b8b and launched an attack on the target contract in the new contract.
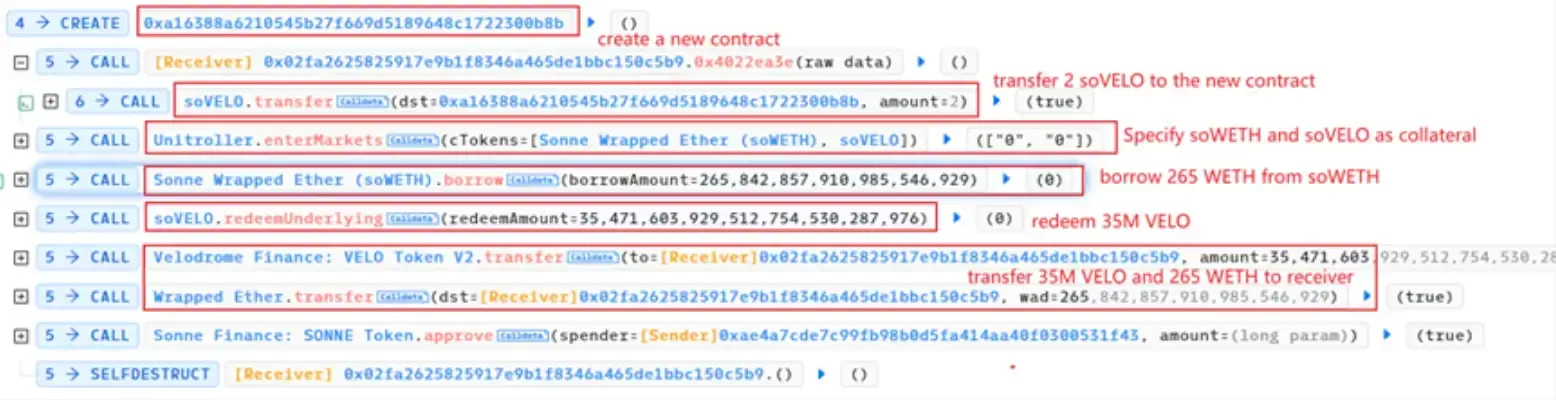
The attack contract followed this process:- Transfer of 2 soVELO to the new contract
- Declare soWETH and soVELO as the collateral
- Borrow 265,842,857,910,985,546,929 WETH from soWETH
From the execution of the borrow function, based on the return value of the getAccountSnapshot function, we can observe:
For the soWETH contract, the updated contract balance is 0, with a loan amount of 0, and an exchange rate (exchangeRate) of 208,504,036,856,714,856,032,085,073.
- For the soVELO contract, the updated contract balance is 2 (with 2 wei of soVELO mortgaged), a loan amount of 0, and an exchange rate (exchangeRate) of 17,735,851,964,756,377,265,143,988,000,000,000,000,000.
exchangeRate is calculated as follows:
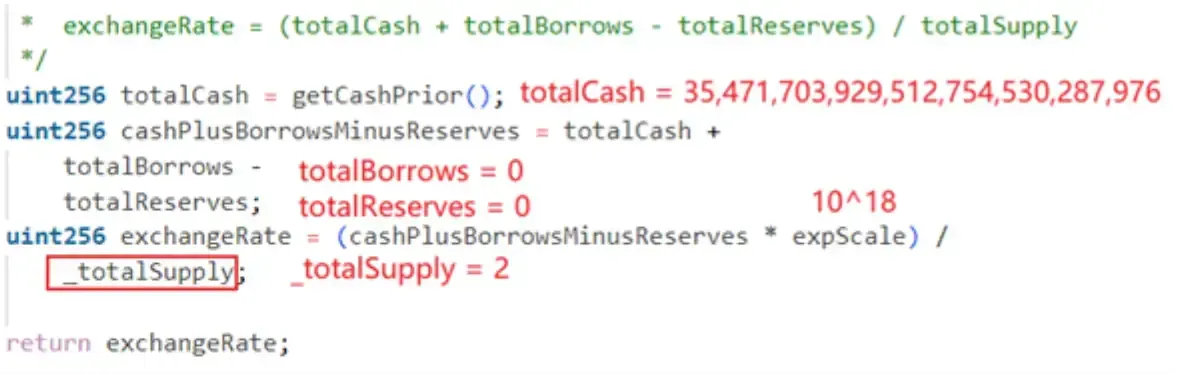
The amount of WETH that can be borrowed by soVELO with 1wei pledged is as follows:1 * exchangeRate * soVELOPrice / soWETHPrice = 763,916,258,364,900,996,923 about 763 WETH. Only 1wei of soVELO mortgage is enough to support this loan.
To borrow 265,842,857,910,985,546,929 WETH (approximately 265 WETH) and convert it into collateral soVELO, the minimum amount of soVELO required to be collateral is:
265,842,857,910,985,546,929 * soWETHPrice / soVELOPrice / exchangeRate = 0.348
That is, 1wei of soVELO collateral is enough.
In fact, only 1wei of soVELO collateral was used when borrowing.
The attacker redeemed the underlying assets, namely 35,471,603,929,512,754,530,287,976 VELO. The amount of collateral soVELO required to redeem 35,471,603,929,512,754,530,287,976 VELO is 35,471,603,929,512,754,530,287,976 * 1e18 / exchangeRate = 1.99999436.
During the calculation, because the calculation uses truncation instead of rounding, the actual calculated required collateral is 1wei of soVELO.
The actual collateral is 2wei of soVELO, of which 1wei is used for the above loan of 265WETH, and the remaining 1wei is used to redeem 35M VELO.
Transfer the borrowed 265 WETH and the redeemed 35M VELO to the attack contract.
- Repeat 3 times (4 times in total) to create a new contract and repeat the attack.
Finally, repay the flash loan.
Flow of Funds
Details

After the Exploit
Sonne Finance became aware of the situation 25 minutes later when the hacker had already stolen $20 million in WETH, Velo (VELO), soVELO and Wrapped USDC (USDC.e) and announced the exploit through their X handle.
How could they have prevented the exploit?
During the project's design and development process, it is crucial to maintain the integrity and rigor of the logic. This includes addressing issues related to deposits, pledges, updating state variables, and handling the trade-offs in multiplication and division calculations. It's important to consider as many scenarios as possible to ensure the logic is comprehensive and free of loopholes.
A full-fledged comprehensive audit of all the contracts in the protocol should be carried out by experts before launching.
Why QuillAudits For Web3 Security?
- QuillAudits is well-equipped with tools and expertise to provide cybersecurity solutions saving the loss of hundreds of protocols in funds.
- Our team of highly skilled auditors have secured over 1M lines of code and $3B in amount.
- Over the course of multiple years, QuillAudits has been proven to be one of the top choices for protocols to get their codebases audited.
Partner with QuillAudits
- OG Program (Opportunities for Listing Managers, KOLs, Top Advisors and Investors with access to early stage Web3 projects)
- QuillAudits Partnership Programme (Venture funds, launchpads, development companies, marketing firms, web2 cybersecurity firms, web3 products)
- WAGSI Program(Claim audit credits to avail exclusive discounts on our auditing package, and additional credits for our automated web3 security infra- QuillShield)